In the previous blog post, we have build and flashed the sample application for disco_l475_iot1 board using Zephyr RTOS. In this post we are going to build and flash the same sample application with MCUboot (Bootloader).
What is a MCUboot?
Here, MCU stands for Microcontroller and boot stands for bootloader which provides a secure firmware upgrade for 32-bit microcontroller. To build a MCUboot with Zephyr the board should have the flash partitions defined in it’s device tree. The partitions are:
- boot_partition
- slot0_partition
- slot1_partition
- scratch_partition
boot_partition
boot_partition contains the bootloader code for securely booting the application image, swapping the application image between slot0 and slot1.
slot0_partition
slot0_partition contains the application image. Once the bootloader is booted it will search the application image available in the primary partition(slot0_partition). After finding the application it will securely boot the image.
slot1_partition
This is a secordary partition, where the firmware upgrade image get stored. Zephyr application which receives the firmware upgrade via serial, bluetooth and other communication protocol, get stored in the secondary partition(slot1_partition).
Note: The size of the slot0_partition and slot1_partition should be same.
scratch_partition
This is a partition, where image get stored temporarily for swapping the image between the slot0 and slot1 partition.
Let’s get started
If you didn’t have any prior experience with Zephyr, please follow the previous blog to setup the development environment, build and flash the sample application.
Clone the MCUboot repository with the following commands:
cd $HOME cd zephyrproject git clone https://github.com/JuulLabs-OSS/mcuboot cd mcuboot
Install the python dependencies by following command:
pip3 install --user -r scripts/requirements.txt
Build and flash MCUboot bootloader
Build the MCUboot bootloader with Zephyr and flash the bootloader to the board
west build -s boot/zephyr -b disco_l475_iot1 west flash
Once the bootloader is flashed open the device’s serial monitor by following command
minicom -b 115200 -D /dev/ttyACM0
If everything goes right, it will display the following output.
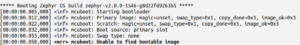
The above image describes the bootloader is successfully flashed. Since the slot0_partition (primary parttion) does not contain’s any signed application image, it’s through an error message in last line.
Follow this steps to flash the sample application (signed image) with zephyr.
cd $HOME cd zephyrproject/zephyr/samples/basic/blinky
Open the prj.conf file
vi prj.conf
And include the following line and save the file
CONFIG_BOOTLOADER_MCUBOOT=y
Build the application
cd $ZEPHYR_BASE west build -b disco_l475_iot1 samples/basic/blinky/
Generated output can be found in the build directory
build/zephyr/zephyr.{bin, hex, elf}
Signing the builded Image
Since the MCUboot is a secure bootloader we need to sign the generated application image with the private key.
cd ../mcuboot/scripts ./imgtool.py sign --key ../root-rsa-2048.pem --header-size 0x200 -S 0x6000 --align 8 --version 1.2 ../../zephyr/build/zephyr/zephyr.hex signed-zephyr.hex
Once the image is signed using imgtool.py flash the image using west.
cd ../ west flash --hex-file scripts/signed-zephyr.hex
Open the serial monitor to check the output.
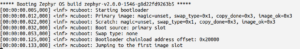
![]()
Here Bootloader chainload address offset: 0x20000, denotes the starting address of the slot0_partition. Here bootloader transfer it’s control to application image. It will blink the on board LED every second.
Conclusion
In this post we build and flashed the sample application using mcuboot with available key in the repository. In this next blog post we will build and flash the image with custom keys.
Reference:
MCUboot: https://github.com/JuulLabs-OSS/mcuboot





